Порівняльне дослідження реалізації блокових шифрів для пристроїв з обмеженими ресурсами (огляд)
DOI:
https://doi.org/10.20535/S0021347023050011Ключові слова:
легкі блокові шифри, FPGA, шифрування, розшифрування, криптографіяАнотація
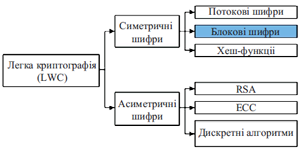
Легка криптографія LWC (LightWeight Cryptography) має вирішальне значення для захисту даних обміну між пристроями з обмеженими ресурсами. У статті розглянуто апаратні реалізації блокових шифрів BC (block ciphers). Детально описані BC з використанням структур мережі перестановки заміни SPN (Substitution Permutation Network) і мережі Фейстеля FN (Feistel network). Надано короткий опис деяких BC на основі структур SPN і FN. Крім того, у статті проведено порівняння та детальний аналіз продуктивності сучасних BC на базі SPN та FN. Для кожного блокового шифру порівнюються такі показники продуктивності, як площа чіпа (кількість модулів), частота, затримка, пропускна здатність і ефективність використання обладнання. В статті також наведені рекомендації щодо використання відповідних шифрів з більш та менш оптимальними показниками продуктивності. Серед різних BC шифр PRINCE має мінімальну затримку та велику пропускну здатність. Дослідження також показало, що шифри LED і PRESENT більш компактні, ніж інші шифри. Також наведено напрямки для подальших перспективних досліджень.
Посилання
- I. Bhardwaj, A. Kumar, M. Bansal, “A review on lightweight cryptography algorithms for data security and authentication in IoTs,” in 2017 4th International Conference on Signal Processing, Computing and Control (ISPCC), 2017, pp. 504–509, doi: https://doi.org/10.1109/ISPCC.2017.8269731.

- C. Pei, Y. Xiao, W. Liang, X. Han, “Trade-off of security and performance of lightweight block ciphers in Industrial Wireless Sensor Networks,” EURASIP J. Wirel. Commun. Netw., vol. 2018, no. 1, p. 117, 2018, doi: https://doi.org/10.1186/s13638-018-1121-6.
- B. J. Mohd, T. Hayajneh, A. V. Vasilakos, “A survey on lightweight block ciphers for low-resource devices: Comparative study and open issues,” J. Netw. Comput. Appl., vol. 58, pp. 73–93, 2015, doi: https://doi.org/10.1016/j.jnca.2015.09.001.
- E. R. Naru, H. Saini, M. Sharma, “A recent review on lightweight cryptography in IoT,” in 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), 2017, pp. 887–890, doi: https://doi.org/10.1109/I-SMAC.2017.8058307.

- G. Hatzivasilis, K. Fysarakis, I. Papaefstathiou, C. Manifavas, “A review of lightweight block ciphers,” J. Cryptogr. Eng., vol. 8, no. 2, pp. 141–184, 2018, doi: https://doi.org/10.1007/s13389-017-0160-y.
- S. Surendran, A. Nassef, B. D. Beheshti, “A survey of cryptographic algorithms for IoT devices,” in 2018 IEEE Long Island Systems, Applications and Technology Conference (LISAT), 2018, pp. 1–8, doi: https://doi.org/10.1109/LISAT.2018.8378034.

- A. Sevin, A. A. O. Mohammed, “A survey on software implementation of lightweight block ciphers for IoT devices,” J. Ambient Intell. Humaniz. Comput., vol. 14, no. 3, pp. 1801–1815, 2023, doi: https://doi.org/10.1007/s12652-021-03395-3.
- Nayancy, S. Dutta, S. Chakraborty, “A survey on implementation of lightweight block ciphers for resource constraints devices,” J. Discret. Math. Sci. Cryptogr., vol. 25, no. 5, pp. 1377–1398, 2022, doi: https://doi.org/10.1080/09720502.2020.1766764.
- L. Sliman, T. Omrani, Z. Tari, A. E. Samhat, R. Rhouma, “Towards an ultra lightweight block ciphers for Internet of Things,” J. Inf. Secur. Appl., vol. 61, p. 102897, 2021, doi: https://doi.org/10.1016/j.jisa.2021.102897.
- H. Luo, W. Chen, X. Ming, Y. Wu, “General differential fault attack on PRESENT and GIFT cipher with Nibble,” IEEE Access, vol. 9, pp. 37697–37706, 2021, doi: https://doi.org/10.1109/ACCESS.2021.3062665.

- T. R. Lee, J. Sen Teh, N. Jamil, J. L. S. Yan, J. Chen, “Lightweight block cipher security evaluation based on machine learning classifiers and active S-boxes,” IEEE Access, vol. 9, pp. 134052–134064, 2021, doi: https://doi.org/10.1109/ACCESS.2021.3116468.

- M. F. Idris, J. Sen Teh, J. L. S. Yan, W.-Z. Yeoh, “A deep learning approach for active S-box prediction of lightweight generalized Feistel block ciphers,” IEEE Access, vol. 9, pp. 104205–104216, 2021, doi: https://doi.org/10.1109/ACCESS.2021.3099802.

- S. Muzaffar, O. T. Waheed, Z. Aung, I. M. Elfadel, “Lightweight, single-clock-cycle, multilayer cipher for single-channel IoT communication: Design and implementation,” IEEE Access, vol. 9, pp. 66723–66737, 2021, doi: https://doi.org/10.1109/ACCESS.2021.3076468.

- V. Yli-Mayry et al., “Diffusional side-channel leakage from unrolled lightweight block ciphers: A case study of power analysis on PRINCE,” IEEE Trans. Inf. Forensics Secur., vol. 16, pp. 1351–1364, 2021, doi: https://doi.org/10.1109/TIFS.2020.3033441.

- S. Kim, J. Kim, S. Kim, D. Hong, J. Sung, S. Hong, “Integral cryptanalysis of lightweight block cipher PIPO,” IEEE Access, vol. 10, pp. 110195–110204, 2022, doi: https://doi.org/10.1109/ACCESS.2022.3214665.

- F. E. Potestad-Ordonez, E. Tena-Sanchez, A. J. Acosta-Jimenez, C. J. Jimenez-Fernandez, R. Chaves, “Design and evaluation of countermeasures against fault injection attacks and power side-channel leakage exploration for AES block cipher,” IEEE Access, vol. 10, pp. 65548–65561, 2022, doi: https://doi.org/10.1109/ACCESS.2022.3183764.

- H. Xiao, L. Wang, “Differential fault analysis on the key schedule of the LBlock algorithm,” IEEE Access, vol. 10, pp. 62402–62411, 2022, doi: https://doi.org/10.1109/ACCESS.2022.3181992.

- S. An, S. C. Seo, “Designing a new XTS-AES parallel optimization implementation technique for fast file encryption,” IEEE Access, vol. 10, pp. 25349–25357, 2022, doi: https://doi.org/10.1109/ACCESS.2022.3155810.

- R. Ghayoula, J. Fattahi, A. Smida, I. El Gmati, E. Pricop, M. Ziadia, “FPGA implementation of SIMON-128 cryptographic algorithm using Artix-7,” in 2022 14th International Conference on Electronics, Computers and Artificial Intelligence (ECAI), 2022, pp. 1–5, doi: https://doi.org/10.1109/ECAI54874.2022.9847520.

- “The performance of various lightweight block ciphers FPGA architectures: A review,” Al-Iraqia J. Sci. Eng. Res., vol. 1, no. 1, 2022, doi: https://doi.org/10.33193/IJSER.1.1.2022.43.
- V. Agate, F. Concone, A. De Paola, P. Ferraro, G. Lo Re, M. Morana, “Bayesian modeling for differential cryptanalysis of block ciphers: A DES instance,” IEEE Access, vol. 11, pp. 4809–4820, 2023, doi: https://doi.org/10.1109/ACCESS.2023.3236240.

- L. Zhao, Y. Chi, Z. Xu, Z. Yue, “Block cipher identification scheme based on Hamming weight distribution,” IEEE Access, vol. 11, pp. 21364–21373, 2023, doi: https://doi.org/10.1109/ACCESS.2023.3249753.

- R. Davis, “The data encryption standard in perspective,” IEEE Commun. Soc. Mag., vol. 16, no. 6, pp. 5–9, 1978, doi: https://doi.org/10.1109/MCOM.1978.1089771.

- J. Nechvatal et al., “Report on the development of the Advanced Encryption Standard (AES),” J. Res. Natl. Inst. Stand. Technol., vol. 106, no. 3, p. 511, 2001, doi: https://doi.org/10.6028/jres.106.023.
- R. Rivest, A. Shamir, L. Adleman, “A method for obtaining digital signatures and public-key cryptosystems (1978),” in Ideas That Created the Future, The MIT Press, 2021, pp. 463–474. DOI 10.7551/mitpress/12274.003.0047
- M. Amara, A. Siad, “Elliptic curve cryptography and its applications,” in International Workshop on Systems, Signal Processing and their Applications, WOSSPA, 2011, pp. 247–250, doi: https://doi.org/10.1109/WOSSPA.2011.5931464.

- U. M. Maurer, “Towards the equivalence of breaking the Diffie-Hellman protocol and computing discrete logarithms,” in Advances in Cryptology — CRYPTO ’94, Berlin, Heidelberg: Springer Berlin Heidelberg, 1994, pp. 271–281. DOI 10.1007/3-540-48658-5_26
- A. Bogdanov et al., “PRESENT: An ultra-lightweight block cipher,” in Cryptographic Hardware and Embedded Systems - CHES 2007, Berlin, Heidelberg: Springer Berlin Heidelberg, 2007, pp. 450–466. DOI 10.1007/978-3-540-74735-2_31
- L. Knudsen, G. Leander, A. Poschmann, M. J. B. Robshaw, “PRINTcipher: A block cipher for IC-printing,” in Lecture Notes in Computer Science, 2010, pp. 16–32. DOI 10.1007/978-3-642-15031-9_2
- J. Guo, T. Peyrin, A. Poschmann, M. Robshaw, “The LED block cipher,” in Cryptographic Hardware and Embedded Systems – CHES 2011, 2011, pp. 326–341, doi: https://doi.org/10.1007/978-3-642-23951-9_22.
- Z. Gong, S. Nikova, Y. W. Law, “KLEIN: A new family of lightweight block ciphers,” in RFID. Security and Privacy, 2012, pp. 1–18. DOI 10.1007/978-3-642-25286-0_1
- D. Engels, M.-J. O. Saarinen, P. Schweitzer, E. M. Smith, “The hummingbird-2 lightweight authenticated encryption algorithm,” in RFID. Security and Privacy, Berlin, Heidelberg: Springer Berlin Heidelberg, 2012, pp. 19–31. DOI 10.1007/978-3-642-25286-0_2
- J. Borghoff et al., “PRINCE – a low-latency block cipher for pervasive computing applications,” in Advances in Cryptology – ASIACRYPT 2012, 2012, pp. 208–225. DOI 10.1007/978-3-642-34961-4_14
- W. Zhang, Z. Bao, D. Lin, V. Rijmen, B. Yang, I. Verbauwhede, “RECTANGLE: a bit-slice lightweight block cipher suitable for multiple platforms,” Sci. China Inf. Sci., vol. 58, no. 12, pp. 1–15, 2015, doi: https://doi.org/10.1007/s11432-015-5459-7.
- D. J. Wheeler, R. M. Needham, “TEA, a tiny encryption algorithm,” in International Workshop on Fast Software Encryption, 1995, pp. 363–366, doi: https://doi.org/10.1007/3-540-60590-8_29.
- J.-P. Kaps, “Chai-Tea, cryptographic hardware implementations of xTEA,” in International Conference on Cryptology in India, 2008, pp. 363–375, doi: https://doi.org/10.1007/978-3-540-89754-5_28.
- D. Hong et al., “HIGHT: A new block cipher suitable for low-resource device,” in International Workshop on Cryptographic Hardware and Embedded Systems, 2006, pp. 46–59, doi: https://doi.org/10.1007/11894063_4.
- C. De Cannière, O. Dunkelman, M. Knežević, “KATAN and KTANTAN — a family of small and efficient hardware-oriented block ciphers,” in International Workshop on Cryptographic Hardware and Embedded Systems, 2009, pp. 272–288, doi: https://doi.org/10.1007/978-3-642-04138-9_20.
- T. Shirai, K. Shibutani, T. Akishita, S. Moriai, T. Iwata, “The 128-bit blockcipher CLEFIA (extended abstract),” in International Workshop on Fast Software Encryption, 2007, pp. 181–195, doi: https://doi.org/10.1007/978-3-540-74619-5_12.
- W. Wu, L. Zhang, “LBlock: A lightweight block cipher,” in International Conference on Applied Cryptography and Network Security, 2011, pp. 327–344, doi: https://doi.org/10.1007/978-3-642-21554-4_19.
- R. Beaulieu, D. Shors, J. Smith, S. Treatman-Clark, B. Weeks, L. Wingers, “The SIMON and SPECK lightweight block ciphers,” in Proceedings of the 52nd Annual Design Automation Conference, 2015, pp. 1–6, doi: https://doi.org/10.1145/2744769.2747946.
- S. P. Guruprasad, B. S. Chandrasekar, “An evaluation framework for security algorithms performance realization on FPGA,” in 2018 IEEE International Conference on Current Trends in Advanced Computing (ICCTAC), 2018, pp. 1–6, doi: https://doi.org/10.1109/ICCTAC.2018.8370396.

- C. A. Lara-Nino, A. Diaz-Perez, M. Morales-Sandoval, “Lightweight hardware architectures for the present cipher in FPGA,” IEEE Trans. Circuits Syst. I Regul. Pap., vol. 64, no. 9, pp. 2544–2555, 2017, doi: https://doi.org/10.1109/TCSI.2017.2686783.

- R. Bharathi, N. Parvatham, “Light-weight present block cipher model for IoT security on FPGA,” Intell. Autom. Soft Comput., vol. 33, no. 1, pp. 35–49, 2022, doi: https://doi.org/10.32604/iasc.2022.020681.
- B. Rashidi, “Flexible structures of lightweight block ciphers PRESENT, SIMON and LED,” IET Circuits, Devices Syst., vol. 14, no. 3, pp. 369–380, 2020, doi: https://doi.org/10.1049/iet-cds.2019.0363.
- T. Okabe, “Efficient FPGA implementations of PRINTCIPHER,” J. Emerg. Technol. Innov. Res., vol. 13, no. 4, pp. 76–85, 2016, uri: https://www.jetir.org/view?paper=JETIR1604017.
- N. Nalla Anandakumar, T. Peyrin, A. Poschmann, “A very compact FPGA implementation of LED and PHOTON,” in International Conference on Cryptology in India, 2014, pp. 304–321, doi: https://doi.org/10.1007/978-3-319-13039-2_18.
- P. Singh, B. Acharya, R. K. Chaurasiya, “High throughput architecture for KLEIN block cipher in FPGA,” in 2019 9th Annual Information Technology, Electromechanical Engineering and Microelectronics Conference (IEMECON), 2019, pp. 64–69, doi: https://doi.org/10.1109/IEMECONX.2019.8877021.

- T. Harikrishnan, C. Babu, “Cryptanalysis of hummingbird algorithm with improved security and throughput,” in 2015 International Conference on VLSI Systems, Architecture, Technology and Applications (VLSI-SATA), 2015, pp. 1–6, doi: https://doi.org/10.1109/VLSI-SATA.2015.7050460.

- A. A. Abdullah, N. R. Obeid, “Efficient implementation for PRINCE algorithm in FPGA based on the BB84 protocol,” J. Phys. Conf. Ser., vol. 1818, no. 112216, 2021, doi: https://doi.org/10.1088/1742-6596/1818/1/012216.
- S. Feizi, A. Nemati, A. Ahmadi, V. A. Makki, “A high-speed FPGA implementation of a bit-slice ultra-lightweight block cipher, RECTANGLE,” in 2015 5th International Conference on Computer and Knowledge Engineering (ICCKE), 2015, pp. 206–211, doi: https://doi.org/10.1109/ICCKE.2015.7365828.

- J. G. Pandey, A. Laddha, S. D. Samaddar, “A lightweight VLSI architecture for RECTANGLE cipher and its implementation on an FPGA,” in 2020 24th International Symposium on VLSI Design and Test (VDAT), 2020, pp. 1–6, doi: https://doi.org/10.1109/VDAT50263.2020.9190623.

- R. Anusha, V. Veena Devi Shastrimath, “LCBC-XTEA: High throughput lightweight cryptographic block cipher model for low-cost RFID systems,” in Cybernetics and Automation Control Theory Methods in Intelligent Algorithms, 2019, pp. 185–196, doi: https://doi.org/10.1007/978-3-030-19813-8_20.
- B. Rashidi, “High-throughput and lightweight hardware structures of HIGHT and PRESENT block ciphers,” Microelectron. J., vol. 90, pp. 232–252, 2019, doi: https://doi.org/10.1016/j.mejo.2019.06.012.
- P. W. Shaikh, I. W. Damaj, “Analysis of pipelined KATAN ciphers under handle-C for FPGAs,” in 2018 International Conference on Innovations in Information Technology (IIT), 2018, pp. 163–168, doi: https://doi.org/10.1109/INNOVATIONS.2018.8606012.

- X. Cheng, H. Zhu, Y. Xu, Y. Zhang, H. Xiao, Z. Zhang, “A reconfigurable and compact hardware architecture of CLEFIA block cipher with multi-configuration,” Microelectron. J., vol. 114, p. 105144, 2021, doi: https://doi.org/10.1016/j.mejo.2021.105144.
- K. R. Aljazeera, R. Nandakumar, S. B. Ershad, “Design and characterization of LBlock cryptocore,” in 2016 International Conference on Signal Processing, Communication, Power and Embedded System (SCOPES), 2016, pp. 166–172, doi: https://doi.org/10.1109/SCOPES.2016.7955732.

- S. Abed, R. Jaffal, B. Mohd, M. Alshayeji, “FPGA modeling and optimization of a SIMON lightweight block cipher,” Sensors, vol. 19, no. 4, p. 913, 2019, doi: https://doi.org/10.3390/s19040913.
- P. Ahir, M. Mozaffari-Kermani, R. Azarderakhsh, “Lightweight architectures for reliable and fault detection Simon and speck cryptographic algorithms on FPGA,” ACM Trans. Embed. Comput. Syst., vol. 16, no. 4, pp. 1–17, 2017, doi: https://doi.org/10.1145/3055514.
- T. Ashur, A. Luykx, “An account of the ISO/IEC standardization of the Simon and speck block cipher families,” in Security of Ubiquitous Computing Systems, Cham: Springer International Publishing, 2021, pp. 63–78. DOI 10.1007/978-3-030-10591-4_4
- A. Nemati, S. Feizi, A. Ahmadi, V. A. Makki, “A low-cost and flexible FPGA implementation for SPECK block cipher,” in 2015 12th International Iranian Society of Cryptology Conference on Information Security and Cryptology (ISCISC), 2015, pp. 42–47, doi: https://doi.org/10.1109/ISCISC.2015.7387896.

- A. Kaur, G. Singh, “Encryption algorithms based on security in IoT (Internet of Things),” in 2021 6th International Conference on Signal Processing, Computing and Control (ISPCC), 2021, pp. 482–486, doi: https://doi.org/10.1109/ISPCC53510.2021.9609495.

- R. S. Salman, A. K. Farhan, A. Shakir, “Lightweight modifications in the advanced encryption standard (AES) for IoT applications: A comparative survey,” in 2022 International Conference on Computer Science and Software Engineering (CSASE), 2022, pp. 325–330, doi: https://doi.org/10.1109/CSASE51777.2022.9759828.

##submission.downloads##
Опубліковано
Як цитувати
Номер
Розділ
Ліцензія
Авторське право (c) 2023 Вісті вищих учбових закладів. РадіоелектронікаИздатель журнала Известия высших учебных заведений. Радиоэлектроника (сокр. "Известия вузов. Радиоэлектроника"), Национальный технический университет Украины "Киевский политехнический институт", учитывает, что доступ автора к его статье является важным как для самого автора, так и для спонсоров его исследований. Мы представлены в базе издателей SHERPA/RoMEO как зеленый издатель (green publisher), что позволяет автору выполнять самоархивирование своей статьи. Однако важно, чтобы каждая из сторон четко понимала свои права. Просьба более детально ознакомиться с Политикой самоархивирования нашего журнала.
Политика оплаченного открытого доступа POA (paid open access), принятая в журнале, позволяет автору выполнить все необходимые требования по открытому доступу к своей статье, которые выдвигаются институтом, правительством или фондом при выделении финансирования. Просьба более детально ознакомиться с политикой оплаченного открытого доступа нашего журнала (см. отдельно).
Варианты доступа к статье:
1. Статья в открытом доступе POA (paid open access)
В этом случае права автора определяются лицензией CC BY (Creative Commons Attribution).
2. Статья с последующим доступом по подписке
В этом случае права автора определяются авторским договором, приведенным далее.
- Автор (каждый соавтор) уступает Издателю журнала «Известия высших учебных заведений. Радиоэлектроника» НТУУ «КПИ» на срок действия авторского права эксклюзивные права на материалы статьи, в том числе право на публикацию данной статьи издательством Аллертон Пресс, США (Allerton Press) на английском языке в журнале «Radioelectronics and Communications Systems». Передача авторского права охватывает исключительное право на воспроизведение и распространение статьи, включая оттиски, переводы, фото воспроизведения, микроформы, электронные формы (он- и оффлайн), или любые иные подобные формы воспроизведения, а также право издателя на сублицензирование третьим лицам по своему усмотрению без дополнительных консультаций с автором. При этом журнал придерживается Политики конфиденциальности.
- Передача прав включает право на обработку формы представления материалов с помощью компьютерных программам и систем (баз данных) для их использования и воспроизводства, публикации и распространения в электронном формате и внедрения в системы поиска (базы данных).
- Воспроизведение, размещение, передача или иное распространение или использование материалов, содержащихся в статье должно сопровождаться ссылкой на Журнал и упоминанием Издателя, а именно: название статьи, имя автора (соавторов), название журнала, номер тома, номер выпуска, копирайт авторов и издателя "© Национальный технический университет Украины "Киевский политехнический институт"; © автор(ы)".
- Автор (каждый соавтор) материалов сохраняет все права собственника материалов, включая патентные права на любые процессы, способы или методы и др., а также права на товарные знаки.
- Издатель разрешает автору (каждому соавтору) материалов следующее:
- Право пользоваться печатными или электронными вариантами материалов статьи в форме и содержании, принятыми Издателем для публикации в Журнале. Подробнее см. политики Оплаченного открытого доступа, подписки и самоархивирования.
- Право бесплатно копировать или передавать коллегам копию напечатанной статьи целиком или частично для их личного или профессионального использования, для продвижения академических или научных исследований или для учебного процесса или других информационных целей, не связанных с коммерческими целями.
- Право использовать материалы из опубликованной статьи в написанной автором (соавторами) книге, монографии, учебнике, учебном пособии и других научных и научно-популярных изданиях.
- Право использовать отдельные рисунки или таблицы и отрывки текста из материалов в собственных целях обучения или для включения их в другую работу, которая печатается (в печатном или электронном формате) третьей стороной, или для представления в электронном формате во внутренние компьютерные сети или на внешние сайты автора (соавторов).
- Автор (соавторы) соглашаются, что каждая копия материалов или любая ее часть, распространенная или размещенная ими в печатном или электронном формате, будет содержать указание на авторское право, предусмотренное в Журнале и полную ссылку на Журнал Издателя.
- Автор (соавторы) гарантирует, что материалы являются оригинальной работой и представлены впервые на рассмотрение только в этом Журнале и ранее не публиковались. Если материалы написаны совместно с соавторами, автор гарантирует, что проинформировал их относительно условий публикации материалов и получил их подписи или письменное разрешение подписываться от их имени.
- Если в материалы включаются отрывки из работ или имеются указания на работы, которые охраняются авторским правом и принадлежат третьей стороне, то автору необходимо получить разрешение владельца авторских прав на использование таких материалов в первом случае и сделать ссылку на первоисточник во втором.
- Автор гарантирует, что материалы не содержат клеветнических высказываний и не посягают на права (включая без ограничений авторское право, права на патент или торговую марку) других лиц и не содержат материалы или инструкции, которые могут причинить вред или ущерб третьим лицам. Автор (каждый соавтор) гарантирует, что их публикация не приведет к разглашению секретных или конфиденциальных сведений (включая государственную тайну). Подтверждением этого является Экспертное заключение (см. перечень документов в Правила для авторов).
- Издатель обязуется опубликовать материалы в случае получения статьей положительного решения редколлегии о публикации на основании внешнего рецензирования (см. Политика рецензирования).
- В случае публикации статьи на английском языке в журнале «Radioelectronics and Communications Systems» (Издатель: Аллертон Пресс, США, распространитель Springer) автору (соавторам) выплачивается гонорар после выхода последнего номера журнала года, в котором опубликована данная статья.
- Документ Согласие на публикацию, который подают русскоязычные авторы при подаче статьи в редакцию, является краткой формой данного договора, в котором изложены все ключевые моменты настоящего договора и наличие которого подтверждает согласие автора (соавторов) с ним. Аналогичным документом для англоязычных авторов является Copyright Transfer Agreement (CTA), предоставляемый издательством Allerton Press.
- Настоящий Договор вступает в силу в момент принятия статьи к публикации. Если материалы не принимаются к публикации или до публикации в журнале автор (авторы) отозвал работу, настоящий Договор не приобретает (теряет) силу.



